Introduction
Today, learning happens online more than ever before. E-learning companies make it possible for students to study from their computers, tablets, or phones. With all this learning happening on the internet, there are some sneaky people out there who want to steal information or cause trouble. That’s where cybersecurity comes in.
In this lesson, we’ll talk about how e-learning companies keep your information safe and what they do to make sure you can study without worrying about cyberattacks. We’re learning all about cybersecurity. We’re going to learn what exactly this cybersecurity word is about, and why you should use cybersecurity techniques to protect your business.
Then we’re going to go into a how-to guide. With all the best practices for protecting your business from cybersecurity attacks, we’ll get into an example where we’ll talk about how to make strong passwords, and then we’ll wrap up with a summary.
Challenges online course creators may face if they don’t use cybersecurity for their e-learning companies:
- Without cybersecurity, online course creators risk exposing student and company data to hackers.
- E-learning content can be stolen and distributed illegally without proper security measures.
- Cyberattacks can disrupt course delivery, causing downtime and frustration for students.
- Security breaches can erode trust among students and institutions, damaging the company’s reputation.
- Non-compliance with data protection laws can lead to legal repercussions and fines for e-learning companies.
Video Lesson – Learn How to Protect Yourself from Hackers and Keep Your Business Safe
Who Can Use?
Almost any teacher, professional, or coach can use cybersecurity to protect their files and client data from unauthorized access or theft.
- To secure their website and user data, including implementing strong passwords and regular software updates.
- To safeguard their online cooking courses and recipes by using secure access controls and encryption.
- To ensure the confidentiality of sensitive documents and manuscripts they handle them through secure file storage and email encryption.
This can work for educational businesses like graphic designers, proofreaders, bloggers, and culinary designers.
What Is It?
Cybersecurity for e-learning companies refers to the comprehensive set of practices, measures, and strategies implemented by online education providers to safeguard their digital infrastructure, sensitive data, and overall learning experience from various cyber threats and attacks. This field of cybersecurity focuses specifically on addressing the unique challenges that e-learning platforms and organizations face in the digital realm.
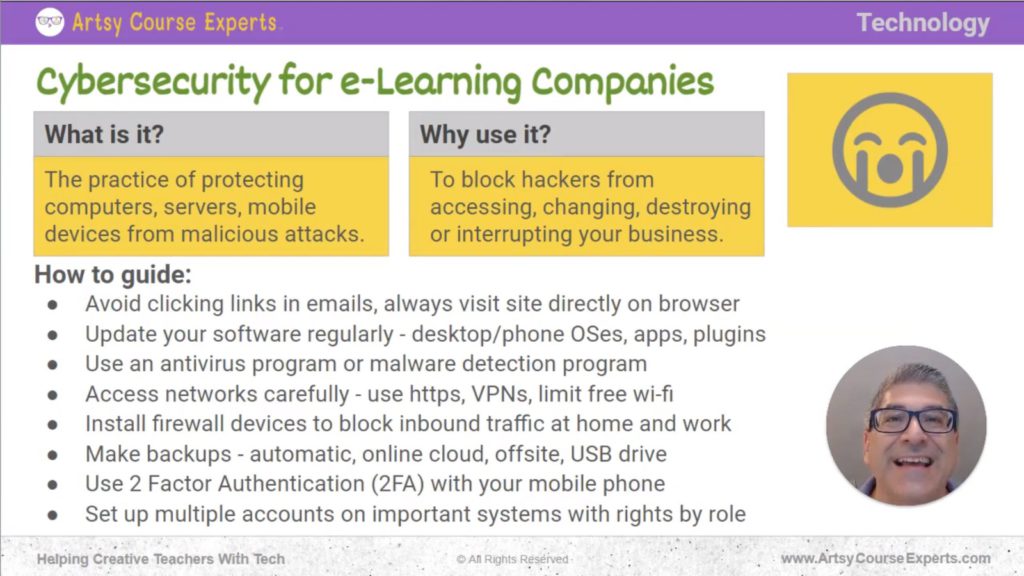
It’s the practice of protecting computers, servers, and mobile devices from malicious attacks, just like a police officer or security guard protects your house or school. They guard doors, look around, watch who comes in and out, and make people sign in. They double-check keys.
In cybersecurity for your business, you want to know who is accessing your systems, who made changes, who is moving files around, adding new ones, taking files out, looking at them, using them, or changing them. That’s what cybersecurity is, and you don’t need to be an IT professional. You can do some basic things and use some tools and external procedures and services to help you out.
Why Use It?
The main reason you would want to use cybersecurity is to block hackers from accessing, changing, destroying, or interrupting your business. You don’t want others accessing your systems, financials, special files with your information, or credit cards. You don’t want them accessing your intellectual property or raw assets because they could share, use, or duplicate them. You don’t want people changing your technology, homepage, course, messaging, email, or forwarding your webpage to another. You don’t want them changing your assets, courses, community information, payment, or affiliate info.
You don’t want people changing anything without your knowledge, and you don’t want anyone destroying your information, shutting down your website, or deleting your files on Google Drive or Microsoft Teams. You don’t want interruptions, like a virus slowing down your website or courses, or your site going down. In the worst case, people could hold you hostage, take over your computer and files, and make you pay ransomware. Cybersecurity can get very ugly, so it’s important to have procedures in place.
How To Guide
Let’s look into a how-to guide with some important things you can do to protect your e-learning business.
Avoid Clicking Links in Emails
Many emails ask you to click a link to update your account, access your password, or unsubscribe. Maybe you don’t want to use the “unsubscribe” link because it tells them your email address is real. Be careful with links in emails you don’t recognize, even if they look familiar. Hover your mouse over them and check the actual address. Verify it’s legitimate. If it seems okay, open your web browser separately and go to that website to check those notifications. If they’re real, they’ll be there.
Update Your Software Regularly
Remember, when bad things happen, companies like Apple, Microsoft, and Google know about it and release software updates. Sometimes it’s an urgent update overnight, or you can schedule it for later. Don’t turn off these updates, and if you can, schedule them for nighttime when you’re not working. Also, think about software on all your devices: desktop, laptop, phone with iOS or Android, apps like Adobe, your web browsers (Chrome, Edge, Safari), and any browser plugins or little apps on your computer. Make sure they all get the updates they need.
Use Antivirus or Malware Detection Software
Try to have antivirus or malware detection software like Norton or Bitdefender. Some stop pop-ups in your browser, while others work in the background on your operating system. They check for suspicious things and ask if you meant to click. Sometimes there might be false alarms, but you can adjust the settings to protect you without annoying you.
If something seems wrong or suspicious, you can raise the settings, do a full scan, and feel secure. It’s great to have these programs installed before a problem arises because some viruses make it hard to install antivirus later. It’s better to get them installed, let them run quietly in the background, and know they’re there when you need them.
Assess Networks Carefully
When you visit a website, there are two ways to go to different pages. There’s HTTP, which is a way to get the text and images from the site. You might not notice, but every time you visit a website, you’re probably using HTTP or HTTPS. The ‘S’ stands for secure, and it’s the one with the lock icon. It’s a good idea to use HTTPS as your default. In the past, it was a bit slower, but these days, it should be fine, even on mobile devices. Using HTTPS should be the standard when you click on things.
When you set up your coaching website, course community, or online course business, make HTTPS the default. It keeps everything secure. Another thing you can do is use a virtual private network (VPN). If you’re in a place like a cafe or airport and using their Wi-Fi, a VPN creates a secure tunnel for your internet traffic. It makes sure no one can see what you’re doing or where you’re from. It might slow things down a bit because your traffic goes through another server, but it’s worth it for the security.
So, when you’re on free Wi-Fi, use HTTPS or turn on a VPN. If you can, limit your use of free Wi-Fi, especially in public places. If you have a mobile device with a hotspot, use that instead.
Install Firewall Devices to Block Inbound Traffic at Home and Work
Install a firewall, like a fancy router at home. You might have a small box from your internet provider, like a modem, but it’s a good idea to have a separate firewall device. This device connects to your internet and might have a few ports and Wi-Fi. It’s like a guard that watches your internet.
Some internet providers give you a router with a built-in firewall, which is great. But if you’re not sure or have a simple internet setup, you can add another device. This firewall device blocks traffic trying to come into your home or workplace. It makes sure no strange data sneaks into your home, like your cameras, devices, computers, or your kids’ devices. The firewall only lets in traffic that you started from inside your home.
If you go to Facebook or your course website from inside your home, the firewall knows you started those sessions. But if some outsider tries to snoop around your home, the firewall stops their data packets from getting in. That’s what a firewall does. It can also block certain types of traffic to keep you safe.
Make Backups
If you need to make a manual backup, set a calendar reminder to copy your files to a USB drive. If something bad happens, having an offsite backup can save the day. It’s there to restore things if you have to wipe your entire computer because of a nasty virus. Automatic backups are the way to go. They work behind the scenes, using an online cloud that’s not even on your computer. It backs up offsite, which is excellent. When your computer has some free time and sees changes, it only uploads those changes. It doesn’t keep uploading all your files constantly.
Having a backup system is important. If you’re a business owner, make sure your team, whether contractors, employees, or yourself, have access to backup options. Maybe you have two computers, one at home and one for when you’re on the go or in the office. Get backups working on all your systems. Sometimes operating systems have backup options, but they might only keep one snapshot. Also, consider using hosting services that offer backups for your websites and other applications. Don’t forget to back up your server computers too.
Use Two-Factor Authentication (2FA) with Your Mobile Phone.
Two-factor authentication adds an extra layer of security when you log into certain accounts, like your bank. When 2FA is on, they’ll send a message to your mobile phone or maybe your email. So, even if someone knows your password, they can’t get in without that extra authentication.
It might be a bit annoying, especially for commonly used accounts, but if you have a big following or think you might be at risk, it’s a good idea to turn on 2FA. In the future, we might need it for everything. Sometimes, 2FA uses email, and sometimes it’s on your phone. There are different systems, but for important accounts like your business or bank, you should use 2FA.
Set Up Multiple Accounts on Important Systems with Rights by Role
Every account can have different roles. For instance, if you’re the owner of your coaching website, you might have an admin account. But when you’re updating the blog, you don’t need to use your admin account. Instead, you can set it aside and use another role, like an editor, for blog updates. If anything goes wrong, you can always go back to your admin account to make changes or remove that secondary role.
Consider having multiple accounts on different systems. In your operating system, there might be an admin account, but for your daily work, you can use a regular user account, especially when you’re using a web browser. You don’t have to log in on your computer or course website as an admin all the time. Reserve the admin role for when you need to do admin tasks, like making big changes, adding or removing courses, or adding applications.
Most of the time, you can use a super editor or power user mode, which is great. If something happens to your main account, and it gets compromised, you can use your power account for other tasks. But you should avoid using your power admin account for everyday activities. Only use it when necessary. It might sound a bit tricky, but as you create websites, communities, and courses, you’ll see that you can create multiple users.
Even if you’re the owner, you might have two levels of access. For your team, consider giving them reduced roles so they can access what they need but avoid giving everyone admin rights. If something were to leak or go wrong, you don’t want too many powerful users out there who could potentially misuse those rights.
Tips: How to Make Strong Passwords
Let’s go over some tips on how to make strong passwords for you and your team.
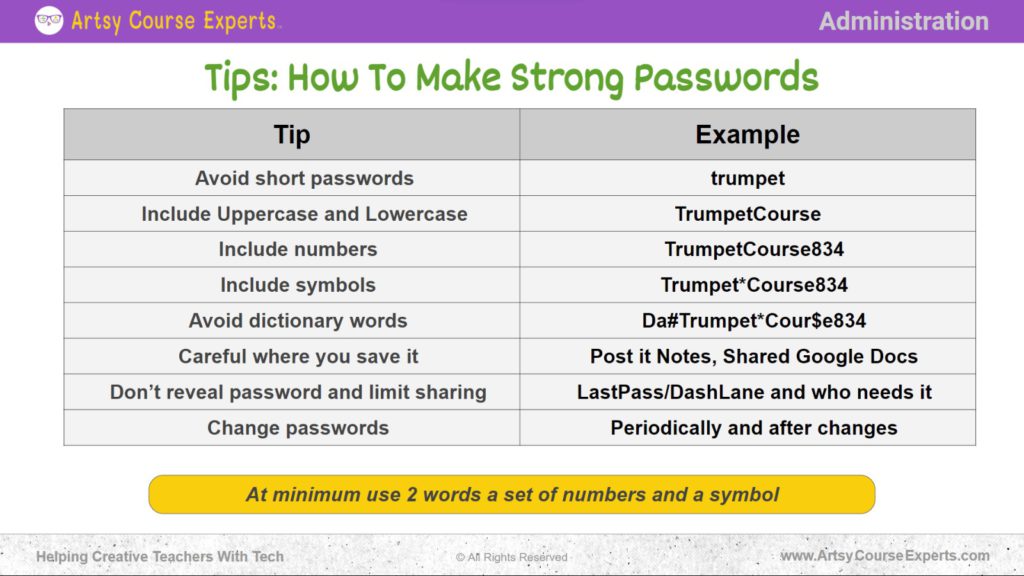
Avoid Short Passwords
These days, passwords with only four, five, or six characters are not enough. Computers can run programs that repeatedly try different passwords until they break in. Some systems might slow down these attacks, but the point is to avoid short passwords. Start thinking about passwords with more than six letters. I know it’s not convenient, but there are too many attacks nowadays. Big companies are using 16-character passwords.
Include Uppercase and Lowercase
Another thing you can do is use both uppercase and lowercase letters. They can be anywhere in the password, not just at the beginning or middle. Maybe you have a certain letter or combination you like, but using both uppercase and lowercase letters creates more combinations. The password has to match exactly, making it harder to guess.
Include Numbers
Don’t just use one digit at the end, like “password1.” Instead, come up with different number combinations. Ideally, use different numbers in different passwords. If one password gets compromised, you don’t want the same number combination to work on another website. You don’t want someone who accesses your website to access your bank, so use different passwords and include numbers, not just one digit but a couple of digits.
Include Symbols
Symbols are additional characters like asterisks, pound signs, exclamation points, or dollar signs. They’re a bit rare, making it harder to guess. Instead of just looping through 26 letters, now you have 26 with uppercase and lowercase, digits, and symbols. It increases the length and complexity of your password.
Avoid Dictionary Words
Hackers have computer programs with lists of popular words like “stapler,” “door,” “window,” “desk,” “light,” etc. They know these words and will try them. Try using less common words or break up your words. Instead of “course” with an “S,” use “course” with a dollar sign. You can also insert some random words, like “trumpet school” with additional sounds like “do,” “re,” “mi,” and “la.” Add extra words that aren’t commonly found in dictionaries, or use unique names from your culture. This makes your password less predictable.
Careful Where You Save It
Don’t just post it on notes on your computer somebody can walk up. That also depends on where you work. But let’s just say they’re on a shared Google doc. Who has access to that? Is it on your computer? Is it on your USB drive with all your passwords? Did you put it in your email? If they get to your email, then they may be able to access to all your passwords. Just think about where you are saving these different passwords, and I like to break them up. I like to have personal passwords and then I have business passwords and then within business passwords.
There are different groups there are passwords for content marketing, and then there are passwords for financial HR legal. Just break them up into different places different places who have different access, et cetera.
Don’t Reveal Password and Limit Sharing
You can use tools like plugins such as LastPass or Dashlane. These allow your contractors and freelancers to access your websites without ever seeing the password. They simply use their browser, go to the website you’ve given them access to, right-click, and fill in the password. They never even know what the password is. If needed, you can change your password, or if they leave, you can revoke their access to those password programs.
In addition, you could limit who gets access to these passwords. Not everyone needs your full list of passwords. Your VA might need one, your social media person might need another, and your instructional designer might need something else. Divide your passwords, tools, apps, and systems and only give people what they need. Don’t just hand out extra passwords. If they need it, they can ask for it, and it won’t be difficult. Having everyone with passwords could lead to risks, not necessarily because they are malicious, but because they create more opportunities. For example, if one of your team members falls victim to a phishing attack and clicks on a suspicious email, it could give someone access to all your files, including your passwords. We don’t want that. Limiting exposure is a smart strategy for your business.
Change Passwords
Periodically, you might want to change your passwords. Maybe you realize one of your passwords was weak or terrible when you first created it. Take the opportunity to level up and create a stronger password. Also, consider changing your password when things change in your team or when new versions of applications come out.
If you’re switching from one service to another, like moving from MailChimp to ConvertKit, don’t use the same old password. Create a new, stronger password each time you update your passwords. This not only keeps your systems secure but also ensures you’re regularly protecting your accounts, not just during emergencies when you have to change dozens of passwords all at once.
Frequently Asked Questions About Using Cyber security for E-learning Companies

Summary – Cybersecurity for E-learning Companies
Cybersecurity is crucial for e-learning companies as it protects sensitive data, course materials, and student information from theft or breaches, ensuring the integrity and trustworthiness of the educational platform. We’ve covered various essential tips to help creative online course creators bolster their cybersecurity measures.
Although cyber threats are a constant concern, implementing these cybersecurity measures and staying vigilant will help online course creators protect their e-learning companies, course materials, and sensitive data, ultimately ensuring a secure and successful journey in the world of online education. Remember, cybersecurity is an ongoing process that requires continuous attention and adaptation to the evolving threat landscape.
Tips for creative online course creators when using cybersecurity for their e-learning companies:
- Regularly update your software and applications for security fixes.
- Implement a robust backup system to safeguard your course materials.
- Enable two-factor authentication for important accounts.
- Keep your devices secure with passcodes or biometrics.
- Educate your team about cybersecurity best practices.
You should be a little smarter now. Thanks for hanging out!
Please subscribe to get more tips for creative online course teachers.
More Tips For Online Teachers
These lessons can also help you with Operations and Technology:
- Backup Tips for Creative Online Course Teachers
- HTTPS Protocol for Creative Business Owners
- When to Upgrade Your Hosting Plan For Creatives
- User Role Settings For Courses, Sites, and Communities